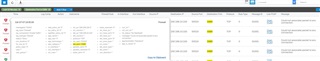
Hello,
Kindly help us please, we have strange traffic drops on our RED branches, their connection to the HQ sometimes get through, and sometimes you need to wait for some times in other words it is erratic, I see these logs and I am very sure that the firewall rule is implemented properly...can anyone please help...we are losing business and the branches are on my shoulder...
The rule: RED ZONE TO HQ LAN ZONE -> ANY SERVICE -ALLOWED (I created an any rule for troubleshooting purposes because maybe I miss some ports, but still we are having the issue)
This thread was automatically locked due to age.