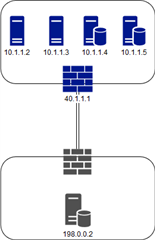
Ok, something that I've easily done many times on all of our UTMs. I have a new IPsec tunnel I built to a 3rd party. We are just accessing a single remote (198.0.0.2/32) host configured in the tunnel, but it needs to be accessed from 4 different hosts on our side. For our "Local Subnet" I need to use our Public/Peer IP (40.1.1.1). How would I go about creating SNAT so each of these 4 hosts source IPs are rewritten as the public/peer IP of our device and then encapped into the tunnel?
I was able to add the single local subnet of our 40.1.1.1/32 peer, and NAT to the private IP (10.1.1.2) of one of the servers and it worked great. How do I go about getting the NAT setup so the other 3 servers can talk too? Looking for help... Is this a Firewall Rule or Business Rule, advanced-firewall? (never understood the need to have separate routing and firewall in the CLI only. What a mess.
This thread was automatically locked due to age.