In log viewer I am noticing a lot of entries allowing traffic to a host for port 3389. This is RDP. There should be no reason for anyone but me to use RDP and I only do it locally or through a VPN tunnel. I created a User/Network Rule intended to drop traffic from specific IP's and IP Networks. You'll notice that the rule shows "in 0 B, out 0 B". The traffic I'm trying to stop still shows as allowed. Any idea what I'm doing wrong?
This is an entry from the firewall log:
This is the Firewall Rule in the top position:
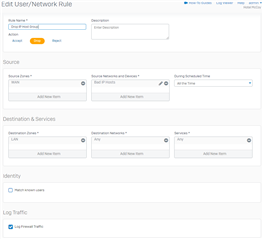
This is the edit page for the firewall rule:
This thread was automatically locked due to age.