Hardware: XG-125
Firmware version: 17.06
----------------------------
Configuration:
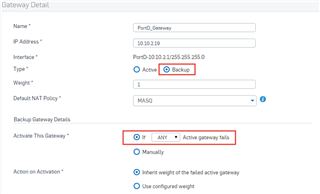
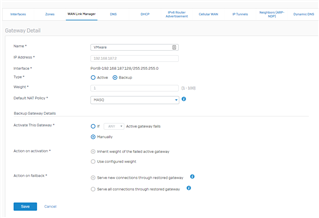
- Gateway 1 - Active, weight 1, connected to a low latency terrestrial connection
- Gateway 2 - Backup, inherit weight from primary, connected to a satellite connection
- Firewall Rule - Primary gateway: Gateway 1 - Backup Gateway: Gateway 2
Behavior:
Failover - Works beautifully. When Gateway 1 fails (pings fail) traffic flips over to Gateway 2.
Failback - When Gateway 1 comes back up, network flows that either failed over to Gateway 2 - or ere already active on Gateway 2 when Gateway 1 came back up DOES NOT failback to Gateway 1.
This is problematic for us because long-lived high-bandwidth flows remain on the satellite network instead of flipping back to the low latency terrestrial connection. Suggestions on how to resolve this and cause flows to failback properly to the primary gateway?
This thread was automatically locked due to age.