Hi
We have an XG230 and an IPSec VPN to a Zywall USG60. The VPN is up an running. After the key lifetime in phase 1 is down the tunnel won't come up automatically.
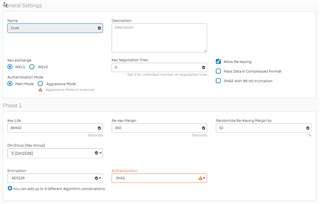
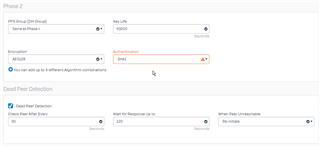
We created a new IPSec policy
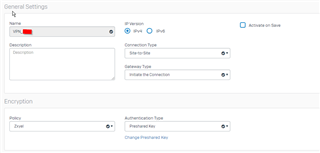
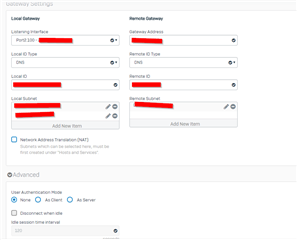
and double-checked the settings on the USG several times.
Same with the settings for the IPSec connection
The adminstrator of the USG told me that he had to activate NAT Traversal. Without this option the tunnel won't come up at all.
Now after 24hrs the tunnel goes down and we need to activate it manually and sometimes we even have to reboot the USG.
In the logs we could find the following:
2018-05-07 07:56:18 20[MGR] <xxx-1|1478> Initiating CHILD_SA with configuration xxx-1
2018-05-07 07:56:18 20[IKE] <xxx-1|1478> initiating Main Mode IKE_SA xxx-1[1478] to IPv4-USG
2018-05-07 07:56:18 20[ENC] <xxx-1|1478> generating ID_PROT request 0 [ SA V V V V V V ]
2018-05-07 07:56:18 20[NET] <xxx-1|1478> sending packet: from IPv4-XG[500] to IPv4-USG[500] (272 bytes)
2018-05-07 07:56:18 20[MGR] <xxx-1|1478> Initiating CHILD_SA with configuration xxx-2
2018-05-07 07:56:18 27[NET] <xxx-1|1478> received packet: from IPv4-USG[500] to IPv4-XG[500] (88 bytes)
2018-05-07 07:56:18 27[ENC] <xxx-1|1478> parsed ID_PROT response 0 [ SA ]
2018-05-07 07:56:18 27[ENC] <xxx-1|1478> generating ID_PROT request 0 [ KE No ]
2018-05-07 07:56:18 27[NET] <xxx-1|1478> sending packet: from IPv4-XG[500] to IPv4-USG[500] (324 bytes)
2018-05-07 07:56:19 21[NET] <xxx-1|1478> received packet: from IPv4-USG[500] to IPv4-XG[500] (91 bytes)
2018-05-07 07:56:19 21[ENC] <xxx-1|1478> parsed INFORMATIONAL_V1 request 2572733315 [ N(AUTH_FAILED) ]
2018-05-07 07:56:19 21[IKE] <xxx-1|1478> received AUTHENTICATION_FAILED error notify
2018-05-07 07:56:19 21[IKE] <xxx-1|1478> IKE_SA AUTHENTICATION_FAILED set_condition COND_START_OVER
2018-05-07 07:56:19 21[IKE] <xxx-1|1478> IKE_SA has_condition COND_START_OVER retry initiate in 60 sec
2018-05-07 07:56:27 28[DMN] [GARNER-LOGGING] (child_alert) ALERT: received IKE message with invalid SPI (507DC9F4) from other side
2018-05-07 07:56:28 25[DMN] [GARNER-LOGGING] (child_alert) ALERT: received IKE message with invalid SPI (507DC9F4) from other side
2018-05-07 07:56:29 13[DMN] [GARNER-LOGGING] (child_alert) ALERT: received IKE message with invalid SPI (507DC9F4) from other side
2018-05-07 07:56:31 05[DMN] [GARNER-LOGGING] (child_alert) ALERT: received IKE message with invalid SPI (507DC9F4) from other side
2018-05-07 07:56:35 11[DMN] [GARNER-LOGGING] (child_alert) ALERT: received IKE message with invalid SPI (507DC9F4) from other side
2018-05-07 07:56:43 16[DMN] [GARNER-LOGGING] (child_alert) ALERT: received IKE message with invalid SPI (507DC9F4) from other side
After successfully reconnecting the two peers we have this error in the log:
2018-05-07 08:22:16 09[APP] <xxx-1|1528> [COP-UPDOWN][SHELL] (run_shell) 'ip route add xxx.xxx.xxx.0/24 dev ipsec0 src xxx.xxx.xxx.1 table 220': error returned 2
But all connections are good for the next 24hrs.
Any ideas?
Does anyone have a proper configuration example?
Regards
Chris
This thread was automatically locked due to age.