Hello,
i have this nasty problem and i don't know to bang my head anymore. I cannot reach a device on a remote site from HQ site and another remote site via IPSEC.
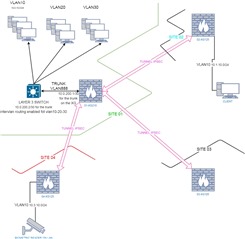
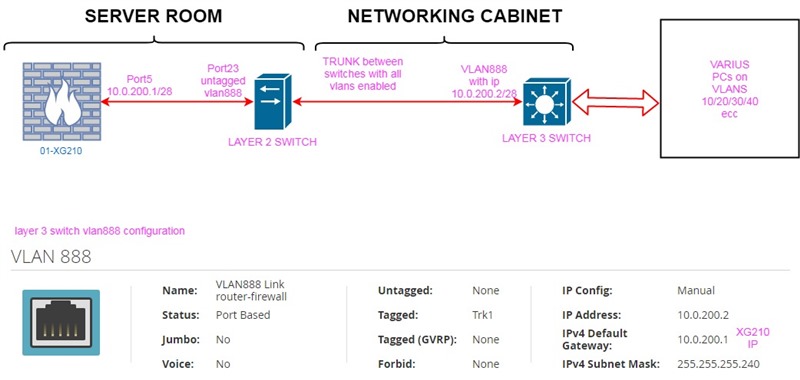
Topology:
Introduction: i have 4 XG in 4 location and a HUB-SPOKE IPSEC VPN setup between HQ and remote branch site.
On the HQ i have an XG210 connected via trunk to a hp layer 3 switch that does all the routing for the vlans in HQ site. On the XG i have a dedicated port (port5) to the switch and they are in a private subnet (10.0.200.0/28).
On the branch sites the XG's do all the intervlan routing themselves.
The problem is: from HQ site (Site01) and from 02 Site i cannot reach a biometric sensor (on a LAN on site 04) with his proprietary program. The strange thing is that i can ping the device and it seems that the routing and firewalls rules are correct.
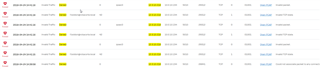
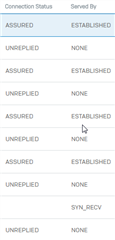
If i use the packet capture on the XG210 (the hub) with the BPF string host 10.3.10.218 (that is the remote biometric sensor) get a lot of assured and unreplied state connection.
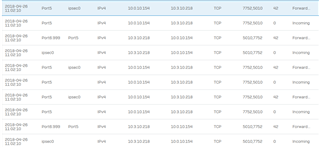
 10.0.10.154 is my pc, 10.3.10.218 is the bio sensor.
10.0.10.154 is my pc, 10.3.10.218 is the bio sensor.
The proprietary program tell me that it can ping the device but it cannot receive any data.
On the 04-xg appliance i get almost the same Assured and unreplied connections.
In the firewall log on the 01 site X210 sometimes i get invalid TCP denials as the firewall cannot identify the connection (like an asymmetric path). BTW since yesterday i didn't receive any error in firewall log anymore, i don't know what of the 1000 rules modification get these errors away...
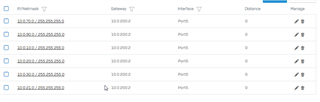
Routing rules on the HQ:
on XG210 i have rules that point the layer 3 switch for his vlans:
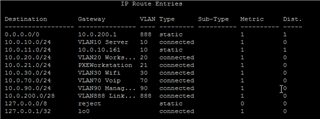
on the switch i have the rules for intervlan routing and then everything that is not known was send back to XG210.
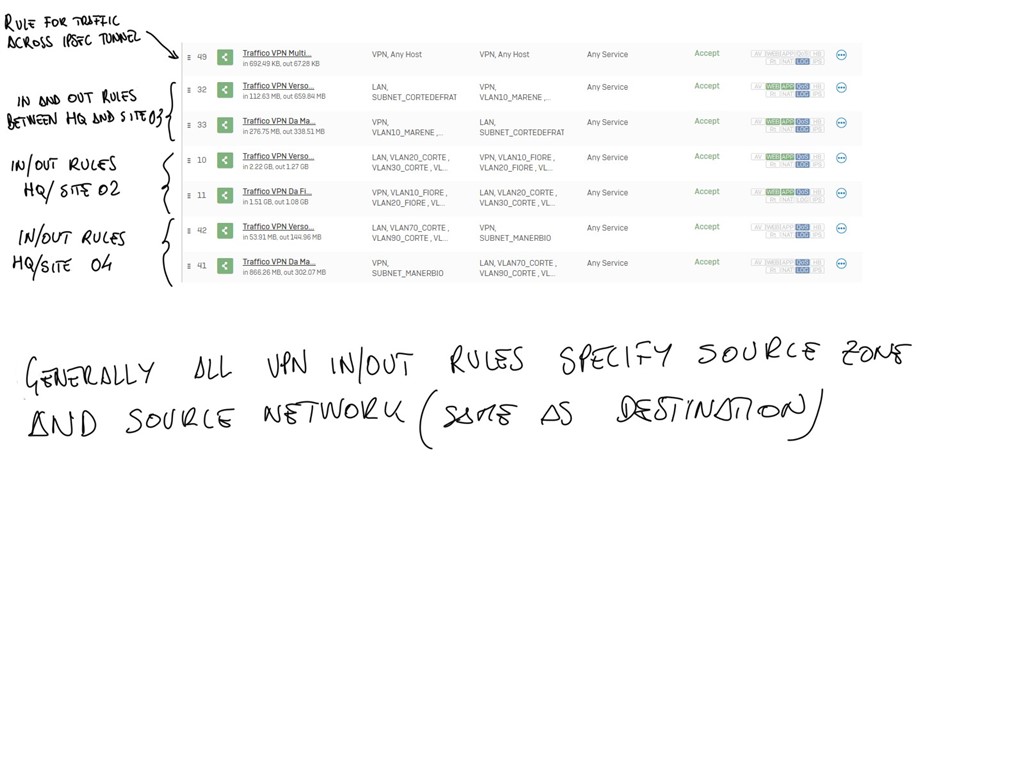
Firewall Rules:
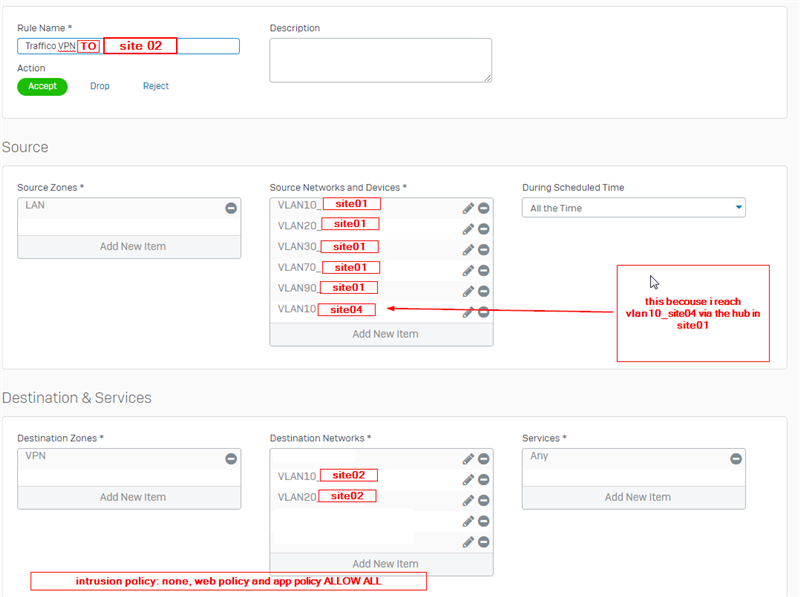
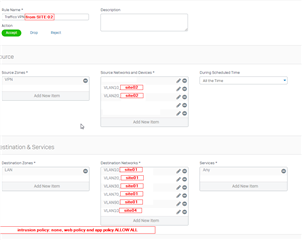
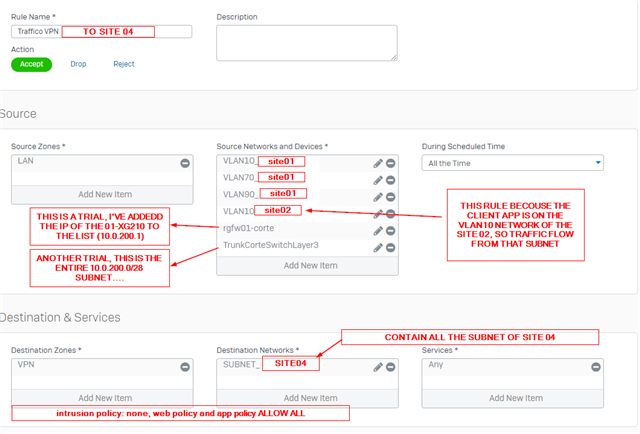
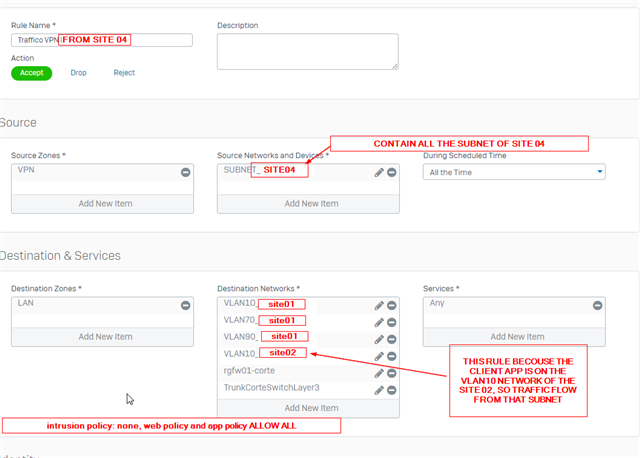
On the HQ i have rules to allow traffic from and to any VPN network (routing between the remote sites so each site can reach in theory other sites, i've followed the Sophos KB with the NY,Dallas,Houston example). Then in have 2 rules for each remote site (in and out traffic) that allow communication with the HQ vlans from VPN sites.
On the branch site i have standard rules that allow everything from VPN interface (any network) to lan interfaces (any networks)
The system is up and running since a year.
In the HQ we have multiple services (exchange,webapp ecc) and this is the first time i have routing problem. Any hint or else to help me to identify the problem? Maybe is the layer 3 switch implementation that is wrong? This is a screenshot from the Network tab on the XG210 of the port that is connected to the switch.
This thread was automatically locked due to age.