Hi People.
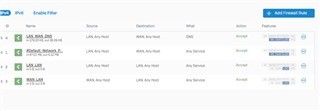
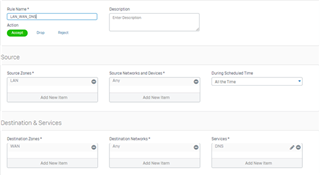
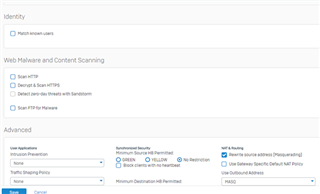
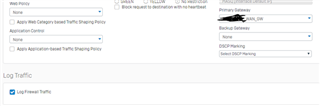
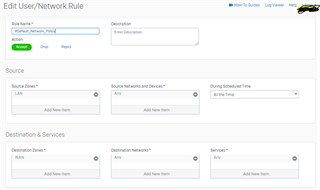
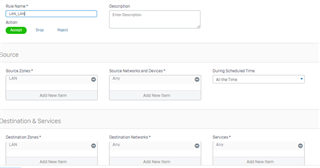
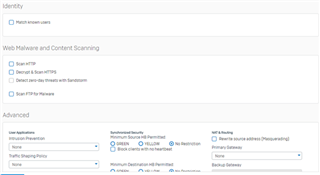
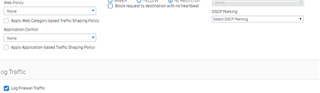
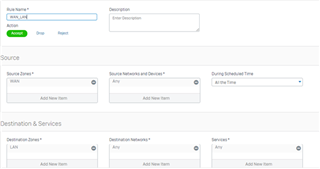
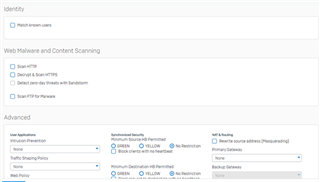
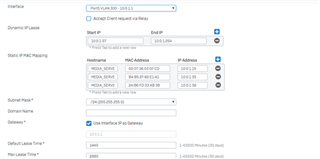
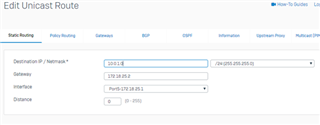
I configure a trunk link between my 3560-CX and the Sophos XG 210 and i know longer can ping/reach the XG's interface. when i change the 3560-CX port to a routed port, i can ping or reach the XG LAN interface. Is this usual?
if it is, how then can i configure my vlans to reach the XG 210?
This thread was automatically locked due to age.