Hi all,
I have already installed a Sophos XG in HA mode in my Workstation.
However, I am using a modem for my Internet connection and I would like to have access from outside to my Sophos via L2TP VPN, Anyone knows which ports/protocols should be open on my public IP address and port forwarding stuff?
I found following information on Sophos Community but it was not complete, however, I added port forwarding for https 4444 and ---- for accessing to the firewall and user profile and they are working except the VPN.
6515 - User Portal. -> It is working
6514 - Admin Portan. -> It is working
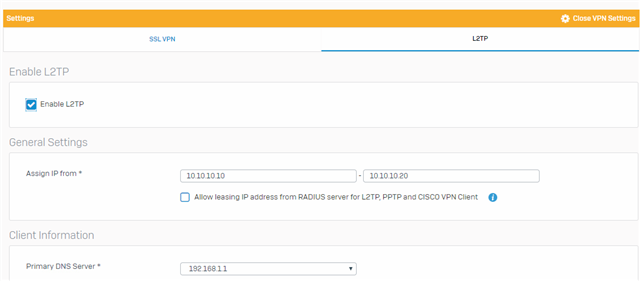
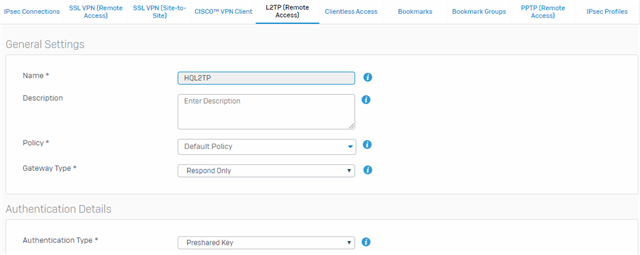
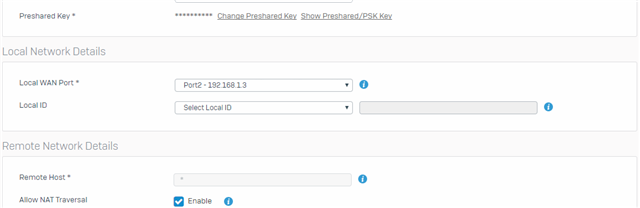
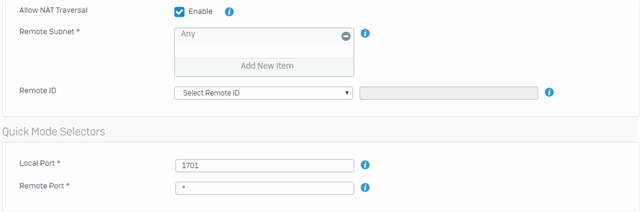
1701 - L2TP. -> Not working
4500 - IPSEC Tunneling. -> Not Working
500 - Ipsec. -> Not working
https://community.sophos.com/products/xg-firewall/f/vpn/76572/step-by-step-l2tp-setup
I am using a FRITZ!Box 7360 and NBN in my home. Here is my modem port forwarding configuration:
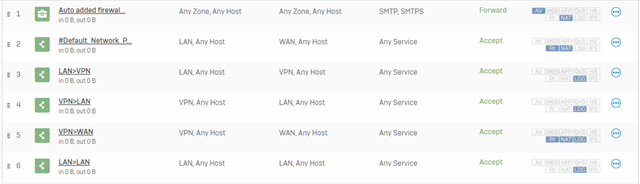
Also, I added these firewall rules on my Sophos as well:
Would you please kindly assist?
Regards,
Sam.
This thread was automatically locked due to age.