Hi all,
I am going to be deploying some AC55C's and need some guidance on what is the best method to achieve what I am after.
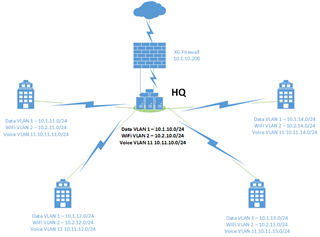
I have a hub and spoke network connected with 5 different sites connected via Metro-Ethernet links, and an XG210 at the main site that serves internet for all. Each site has its own subnet. Data VLAN is 1.
What I would like to achieve is have a "corporate" SSID where the company assets connect (like company laptops, tables, executive's cell phones, etc) that can "see" all the resources on the LAN and is also prioritized appropriately, and a "guest" SSID for visitors to the premises and employees personal phones that is isolated from seeing the company LAN resources and also traffic is prioritized lower; I don't want guests and low priority wireless traffic clogging my WAN and internet links.
I had ASSumed that the way to go about this was to create a corporate SSID and bridge that to the AP LAN, and create a "guest" SSID and bridge that to a VLAN I would create especially for guest WiFi traffic so I could limit it via ACL's and de-prioritize the traffic in my routers, but I realized in the course of this that I don't really know how these AP's work with the XG and perhaps I should look at creating a separate "Zone" instead of bridging it to a VLAN.
The help guide doesn't really provide any deep conceptual explanations and the KnowledgeBase didn't reveal what I was looking for either.
If anyone could chime in I'd appreciate it. Thanks in advance.
This thread was automatically locked due to age.