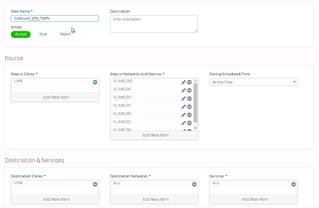
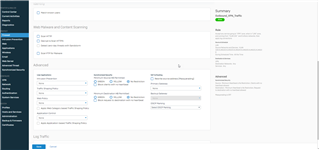
I am having the exact same issue as the below person.
https://community.sophos.com/products/xg-firewall/f/vpn/94105/ipsec-mikrotik-to-sophos-problem
The IPSec tunnel establishes correctly and from the local network behind the Mikrotik can ping the local network behind the Sophos XG Firewall. But from the local network behind the Sophos XG I cannot ping the Mikrotik or the local network behind the Mikrotik. I do not have any policy routes and tried the below command but that did not help.
system ipsec_route add net 192.168.87.0/255.255.255.0 tunnelname <IPSec Tunnel Name>
Any help would be greatly appreciated. Thanks!
[locked by: SupportFlo at 5:53 PM (GMT -8) on 5 Nov 2018]