Hello
I think that there is a misbehaviour concerning VLANs on the XG Platform.
The scenario is:
SFOS 17.0.5 MR5 installed.
Cisco Switch with 2 VLANs (Trunk Port 90,100) connected to the XG LAN Port (Port1).
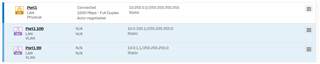
Port 1 (LAN) 10.255.0.2 /32 --> Dummy Adress, field can't be empty
VLAN 1.90: 10.0.1.1 /24 and DHCP 10.0.1.245-10.0.1.254
VLAN 1.100: 10.0.100.1 /24
Port 2 (WAN) 10.0.9.2 /24
Problem 1:
VLAN 90 has a Sonos System, Mobile Phones and a Laptop connected. Mixed with
Static and DHCP addresses. All devices are able to connect to the Internet
and the Mobile Phones play webradio to the Sonos System. So far so good.
Obviously the DHCP server assigns addresses to the devices, but in the DHCP
configuration there are no IP4 leases listed at all.
Problem 2:
Using a Firewall Rule my attempt was to access devices in VLAN 100 from VLAN 90
but I don't get it working the way I'd like to.
Source Zone: LAN
Source Network and Devices: #Port1.90
Destination Zone: LAN
Destination Networks: #Port 1.100
Services: Any
The scenario above doesn't work at all.
Identical behaviour is when I want to limit the traffic to WAN to be from VLAN 90
only (i.e. by modifying the Sophos Standard Rule).
Source Zone: LAN
Source Network and Devices: #Port1.90
Destination Zone: WAN
Destination Networks: Any
Services: Any
The scenario above works only by setting "Source Network and Devices" to "Any".
Otherwiese no device on VLAN 90 can connect to the Internet.
Does anyone have an idea or do I misunderstand the VLAN concept on Sopos?
Thanks for any help.
This thread was automatically locked due to age.