This document covers the use of the new IaC template scanning API endpoint of Sophos Cloud Optix. This is documented here: https://optix.sophos.com/apiDocumentation (In the "APIs for IaC Integration" section)
1. Pre-Requisites
- A Sophos Cloud Optix account
- An Azure DevOps account
2. Enable API on your Sophos Cloud Optix Account
a. Go to https://optix.sophos.com/ and sign in with your credentials
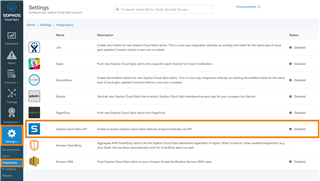
b. Go to Settings → Integrations → Sophos Cloud Optix
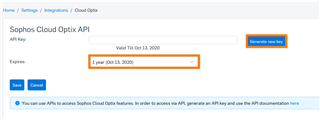
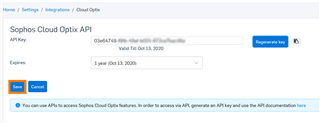
c. Select the expiry time (6 months, 1 year or Never), then click on "Generate new key"
- This needs to be done in Azure DevOps.
- This can be any repository that hosts your IaC templates (ARM, Terraform, e.t.c.)
- This can be for a build pipeline or a release pipeline. The example below uses a release pipeline
- The example below shows how to add an Azure Repo for a release pipeline but this will need to be followed for the source control that you are using and the pipeline that you are configuring
- This needs to be done in Azure DevOps.
- This can be for a build pipeline or a release pipeline. The example below uses a release pipeline.
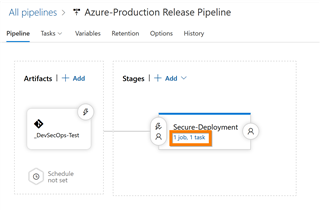
a. Azure DevOps → Pipelines → Releases → Select Pipeline → Edit"
b. Click on the stage that you want to add the IaC template security/compliance validation task to
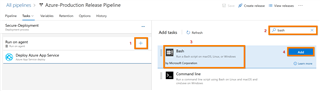
c. Click on "+" to add a new task, search for "bash", then select the "Bash" task
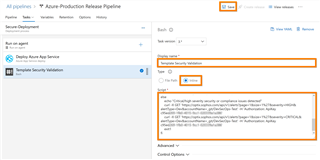
d. Select the task and edit the following
- Display Name: Template Security Validation
- Type: Inline
- Script: Add the sample script content below but edit with the right parameters
- ApiKey: Ensure that you put in your API key
- repo_url: This is the environment name that will be displayed in CLoud Optix if the result is saved
- files: Ensure that this is prefixed with the alias name of your Repo name that you defined in the pipeline artifact
- Click on "Save" (top right corner)
# Scan for any high severity security and compliance issueshighalerts=$(curl "https://optix.sophos.com/api/v1/iac/scan" -H "Authorization: ApiKey c95ed269-xxxx-xxxx-xxxx-xxxxxxxxxxxxxx" -F "repo_url=https://david0620@dev.azure.com/david0620/DevSecOps-Test/_git/DevSecOps-Test" -F "committer_name=DavidOkeyode" -F "committer_email=optixworkshop0919@outlook.com" -F "branch=master" '-F files=@_AzureDeployment-Prod/cloud-optix-demo.json' -F "async=false" | jq '.summary.num_high_alerts'); # Scan for any critical severity security and compliance issuescriticalalerts=$(curl "https://optix.sophos.com/api/v1/iac/scan" -H "Authorization: ApiKey c95ed269-xxxx-xxxx-xxxx-xxxxxxxxxxxxxx" -F "repo_url=https://david0620@dev.azure.com/david0620/DevSecOps-Test/_git/DevSecOps-Test" -F "committer_name=DavidOkeyode" -F "committer_email=optixworkshop0919@outlook.com" -F "branch=master" '-F files=@_AzureDeployment-Prod/cloud-optix-demo.json' -F "async=false" | jq '.summary.num_critical_alerts'); # Stop the pipeline if there are any high or critical security or compliance issues detected# Also print out the issues detected if anyif [[ $highalerts == 0 ]] && [[ $criticalalerts == 0 ]]; then echo "No critical/high severity security or compliance issues was detected"else echo "Critical/high severity security or compliance issues detected" curl -X GET 'https://optix.sophos.com/api/v1/alerts?page=1&size=1%27&severity=HIGH&alertType=Dev&accountName=_git/DevSecOps-Test' -H 'Authorization: ApiKey c95ed269-xxxx-xxxx-xxxx-xxxxxxxxxxxxxx' | jq curl -X GET 'https://optix.sophos.com/api/v1/alerts?page=1&size=1%27&severity=CRITICAL&alertType=Dev&accountName=_git/DevSecOps-Test' -H 'Authorization: ApiKey c95ed269-xxxx-xxxx-xxxx-xxxxxxxxxxxxxx' | jq exit1fi |
e. Ensure that the task is dragged above the main deployment tasks
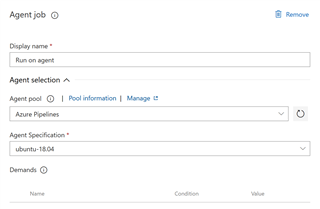
- You can also select the agent that you want to run the task. I used "Ubuntu 16.04" in this example but you can test with others also
5. Test the pipeline
a. Azure DevOps → Pipelines → Releases → Select Pipeline → Create release"
b. Look in the release logs for the output
- Click on the "Template Security Validation" task for full details
- The alerts detected can also be viewed in the Cloud Optix console (this is saved by default but can be modified using a parameter)