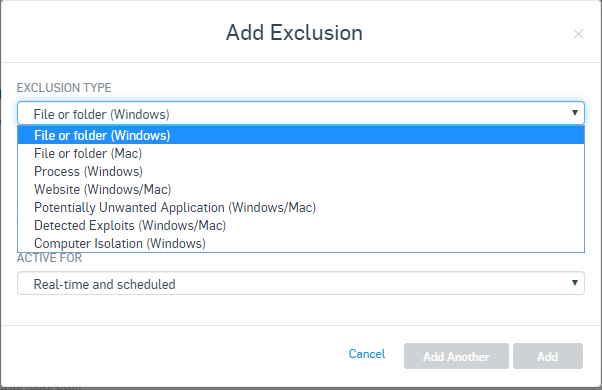
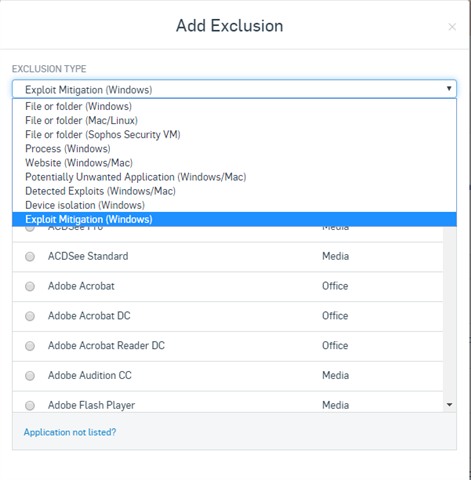
Currently there are only 7/9 Exclusion Types (compared to the 9 Exclusion Types in Global Settings/ Global Exclusions) available when adding an exclusion to a threat protection policy. Why are there less options to create granular exclusions at the policy level, but more options at the global level? This seems backwards, because we would want to be more restrictive closer to the endpoint and not the other way around.
Discussion: In an enterprise environment with many users filling a variety of job requirements, the inability to create granular Exploit Mitigation exclusions makes for a cumbersome exclusion process. Yes, this option is available in Global Exclusions, however we may only want to exclude a certain Exploit Mitigation (i.e. Lockdown exploit) from being detected in a given application (i.e. Excel, Adobe, etc.) for only a handful of tens of thousands of computers. In this case, we would want to create a specific policy for a subset of users to which we could apply this exclusion for.
Because of the unique nature of a detection ID/ thumbprint that is assigned to an exploit mitigation event, creating a custom policy and adding a "Detected Exploits" exclusion is not effective. One example is a user who had a custom script that is run on ever-changing Excel reports. The script that gets run on the report is a PowerShell script, and had a handful of commands that could be run. Different commands generated different detection IDs, thus requiring a custom threat protection policy to be created with 7 Detected Exploit exclusions.
I have submitted a feature request via the ideas portal. Please vote if you agree with the sentiments shared in this discussion post.
Exclusion Types available when making a **Threat Protection Policy** Exclusion in Sophos Central
Exclusion Types available when making a **Global** Exclusion in Sophos Central
This thread was automatically locked due to age.