Here are some recommendations to harden the overall security of your Sophos Firewall.
Table of Contents
- Keep Your Firmware Updated and Hotfixes Enabled
- Limit Firewall Device Access
- Lock Down Remote Access to Other Network Systems
- Use Multi-Factor Authentication and Strong Passwords
- Use Role-Based Administration
- Enable TLS Inspection and Intrusion Prevention
- Enable Firewall System Notifications
- Configure Country Blocking
Keep Your Firmware Updated and Hotfixes Enabled
Every update to Sophos Firewall OS includes important security enhancements and in some cases, important Hotfixes are released between updates. Ensure you keep your firmware up to date and have Hotfixes enabled under Backup & Firmware > Firmware.
Helpful Links:
Limit Firewall Device Access
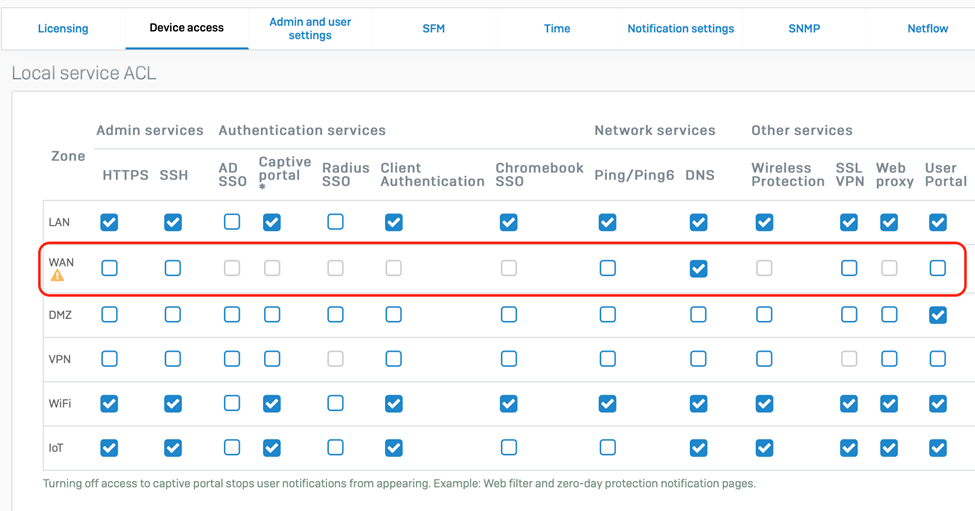
It’s critically important that you disable non-essential services on the WAN interface. In particular, HTTPS and SSH admin services. To manage your Firewall remotely, Sophos Central offers a much more secure solution than enabling WAN admin access. If the User Portal is not being used, we also recommend deactivating this service on the WAN as well.
Check your local services access control under Administration > Device Access and ensure no items are checked for the WAN Zone unless absolutely necessary:
Helpful Links:
- Sophos Firewall: Turn off Web Admin and User Portal access on the WAN zone
- https://docs.sophos.com/nsg/sophos-firewall/18.5/Help/en-us/webhelp/onlinehelp/AdministratorHelp/Administration/DeviceAccess/index.html#local-service-acl-how-device-access-works
- For recommended remote administration options, please consider the following:
Lock Down Remote Access to Other Network Systems
Do NOT expose any systems directly to the internet using NAT or Firewall Rules that allow inbound connections. This includes IoT devices. Review all your NAT and Firewall Rules and ensure there are no WAN to LAN rules. Use VPN or ZTNA only for remote administration and access for internal systems. For IoT devices, shut down any devices that require direct access via NAT and do not offer a cloud proxy service.
Use Multi-Factor Authentication and Strong Passwords
Enable Multi-Factor Authentication or One Time Password (OTP) and enforce strong passwords which will protect your Firewall from unauthorized access either from stolen credentials or brute force hacking attempts
Helpful Links:
Use Role-Based Administration
Take advantage of Sophos Firewall’s granular role-based administration profiles to limit access for administrators of the firewall. Provide read-only access to administrators that don’t absolutely need control over various firewall functions.
Helpful Links:
Enable TLS Inspection and Intrusion Prevention
IPS can help protect against intrusions and Denial of Service attacks, but only if encrypted traffic is inspected. Enable TLS inspection and IPS and ensure it’s configured to automatically update and DoS protection is applied.
Helpful Links:
- https://docs.sophos.com/nsg/sophos-firewall/18.5/Help/en-us/webhelp/onlinehelp/AdministratorHelp/RulesAndPolicies/SSL/TLSInspectionRules/SSLTLSInspectionSettings/index.html
- https://docs.sophos.com/nsg/sophos-firewall/18.5/Help/en-us/webhelp/onlinehelp/AdministratorHelp/IntrusionPrevention/index.html#turn-on-ips-protection
Enable Firewall System Notifications
Sophos Firewall can be configured to alert administrators of system-generated events. Administrators should review the list of events and ensure that key events are monitored to ensure that issues and events can be acted upon promptly. Sophos recommends that you adopt a regular triage and investigation routine to make sure that no events are missed or left to linger too long. Notifications are sent via either an email and/or to SNMP traps. To configure Notifications, navigate to Configure > System services and select the Notifications list tab.
Helpful Links:
Configure Country Blocking
As a security best practice you can further narrow your attack surface area by limiting exposure to regions you don't do business with using country blocking.
Helpful Links:
