I have HQ in Singapore with dual wan over two isps. so eth4 (backupWAN) and eth1 (primaryWAN)
during the initial setup, it was working (ie: i was able to have two ipsec connections, with 1 being active at any time and manually toggled)
now, the site to site vpn connection over the backup wan eth4 cannot be established.
the remote site is in china. I'm wondering is it possible the great firewall of china is listen on one route and screwing it up but not in the other route.
I have asked the isp and they say nothing wrong at their end.
i have tried deleting all the site to site vpn information and re-setup from scratch but it doesn't work. (ie: eth1 is the only functional tunnel).
I noticed this behaviour occured after a firmware update several weeks ago. (probably a 9.4 version )
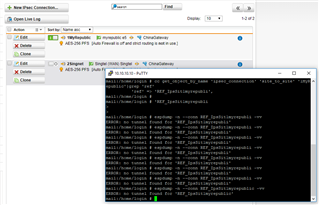
I'll post the redacted logs in the following post.
things I notice
2017:11:17-10:42:09 mail ipsec_starter[7515]: no default route - cannot cope with %defaultroute!!! (this happens with both eth4 and eth1 connections but it still allows the eth1 to form so i think its a non issue)
---this is eth4 failing---
2017:11:17-10:42:09 mail pluto[7528]: ERROR: "S_1HWbackupWAN" #1: sendto on eth4 to 180.111.222.333:500 failed in main_outI1. Errno 1: Operation not permitted
2017:11:17-10:42:09 mail pluto[7528]: | inserting event EVENT_RETRANSMIT, timeout in 10 seconds for #1
--eth1 towards the end of the log will success after i reenabled the ipsec option at the remote site (ie: i turn off all ipsec connections and turn them on again when i switch from eth4 to eth1--
This thread was automatically locked due to age.