Any knowledge about that ?
This thread was automatically locked due to age.
Hallo,
This is possible but very labor-intensive. Why not use the free SSL VPN client (Windows or OpenVPN client for Mac) or a free Sophos IPsec client (Windows & Mac)?
Cheers - Bob
Hi,
Exactly this I'm trying to examine ;-)
Currently I do satisfy my roadies (mac & windows) with l2tp/over ipsec using the builtin os. way and it works mostly ok.
Due to its's legacy approach regarding, performance, overhead, encryption, not split able I think about switching to ipsec not ssl vpn at all and therefore a bunch of questions coming up:
1. Setup Remote Access (Ipsec - UTM - for win&mac) which one ?
Cisco or IPsec - Whats the difference ?
2. Sophos Ipsec client mac and windows ?
The user portal just offers the software for windows but not for mac, where do i get it ?
3. Sophos Ipsec utm setup / ipsec client encyption and split able ?
If I choose ipsec and there is a client for mac & windows is it then possible to use the aes-gcm gain & is it split able ?
Further I am very curious about the performance/latency diff between l2tp over ipsec vs ipsec with the sophos software !?
Please let us know if Sophos Connect supports AES-128 GCM PFS:
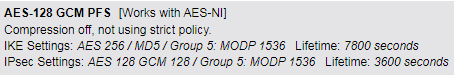
GCM uses hardware acceleration for encryption. Makes this VERRRRY fast if your CPU can do it.
Cheers - Bob
Just curious, would you think about looking into ZTNA as a alternative? www.sophos.com/.../zero-trust-network-access.aspx
__________________________________________________________________________________________________________________
The EAP for the Agentbased Version will start soon. Keep an eye out on the Forum: https://community.sophos.com/zero-trust-network-access/
Essentially it will likely replace the VPN in the future. Simply because with an IDP (like Azure AD) it literally resolve all limitations/challenges of most customers for decades.
It will be integrated with the Sophos Endpoint. Therefore you simply have to use the endpoint and the endpoint will provide the policies. Its a SSO experience (Login to your Windows) and you can access all apps (Web based or application based like SSH, RDP etc.) without any additional window.
Here some more information: https://partnernews.sophos.com/it-it/2020/12/products/sophos-zero-trust-network-access-ztna-is-coming-soon-your-faq/
But essentially you need a virtual machine (As a gateway) and thats it. The rest is in Central and your IDP (Azure).
__________________________________________________________________________________________________________________
Thanks, Toni,
The presentations were for a CEO or a salesman, so one has to read between the lines. It appears that without XG v19 and Central Intercept X, there's really no more security than with a VPN and MFA, or???
Cheers - Bob
ZTNA does not really benefit by a Firewall. ZT (Zero Trust) needs a network segmentation to begin with. This is the job of a firewall, for sure.
But keep in mind, Zero Trust is a concept. You do not trust anybody. Zero Trust is not a product. Feel free to read this: https://medium.com/technology-hits/zero-trust-is-a-concept-not-a-product-introduction-to-zero-trust-security-architecture-zta-3830d782ef5f
A ZTNA product gives you the benefit of not being on the network. Means you do not have a IP and therefore no lateral movement is possible. VPN (+ MFA but it does not matter) does not check the device status. If the device is compromised, you can literally use lateral movement. This is not possible in ZTNA. You only have access to one facility and only via a certain port. You cannot move across and spread.
The endpoint gives you the chance to implement health status, as you can combine the sync sec Story with the ZTNA.
ZTNA as a tech demo is impressive, as you can simplify the issues with certain challenges of most VPN solutions in one shot. You want to publish a new resource? Simply add it to central (Internal IP) --> Done. The rest will be published to the client by Central and the agent tunnels the certain application through Port 443. You can access everything everywhere without to check a VPN status or a connection status. You do not have any limitation of "Will IPSEC, SSLVPN work here?". You do not have the issue with "How do i publish / provide my config?". It does not matter, how many resources you publish, as it only will be used by the user clicking on the resource. Its not a "VPN tunnel is there 24/7 and can be used all the time".
After the publishing of the EAP2, which will include the Agent as well, i would highly recommend to take a look into this product. This is, as most analyst and tech people say, be a game changer.
__________________________________________________________________________________________________________________
Hi Bob,
ahh- unfortunately it looks that I can't test that - see screenshot ;-(
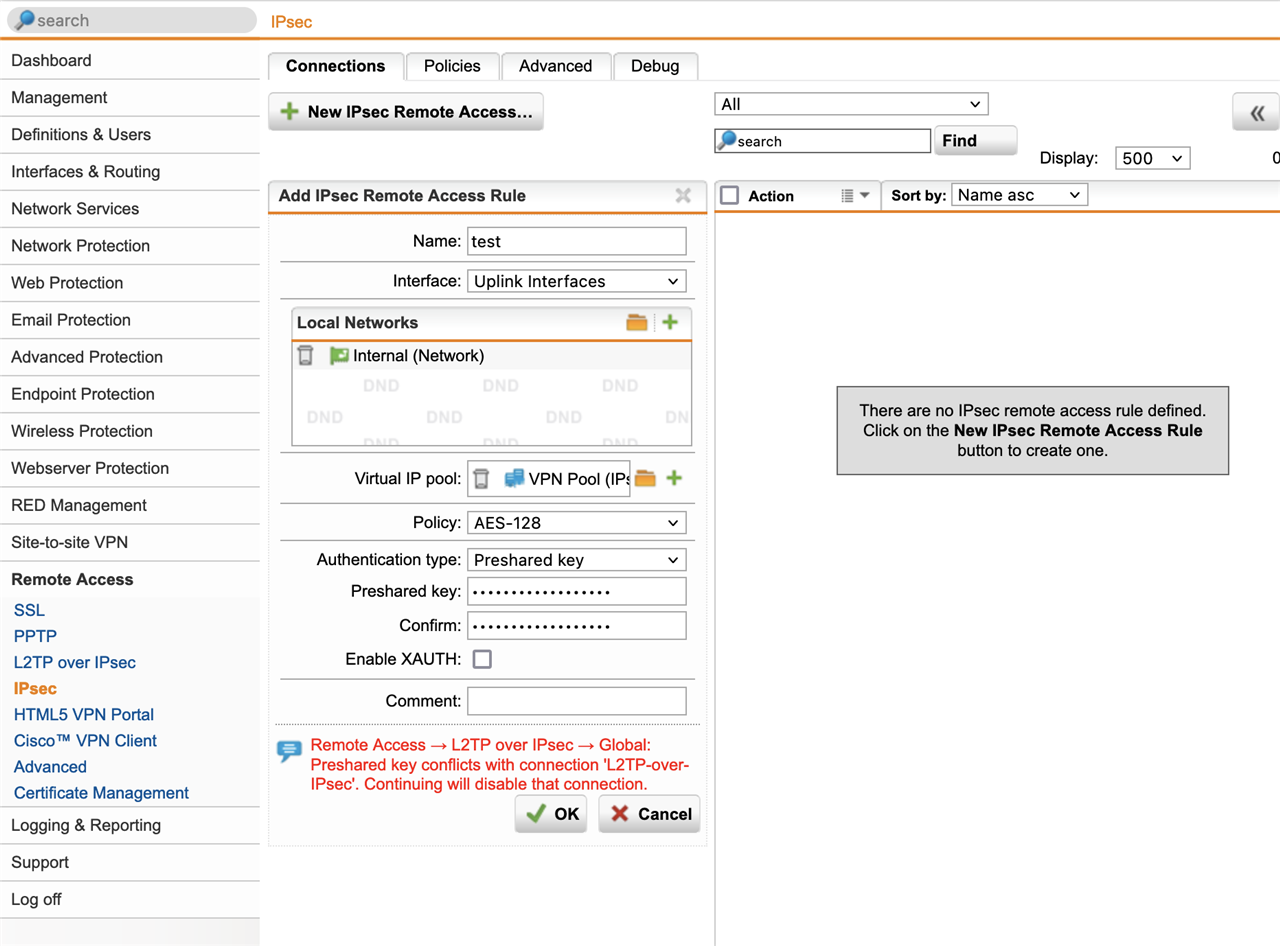
The link you provided refs. to Xg. but do run Sg and for the user portal what we do not use and is then only for windows, also It looks like the client user need to be admin to install the sophos ipsec client ;-( which is not and never the case and I was really not able to find normal download links for mac and windows (...).
How to get the sohos ipsec client software for mac and windows, ideally as msi. + how to get the client ipsec settings except over the user portal to be able to create a script for mass deployment ?
Thanks in advance for all tips and hints !