Sophos UTM Configuration
Interfaces
External (WAN) 82.x.x.x
DMZ 10.0.0.1 /8
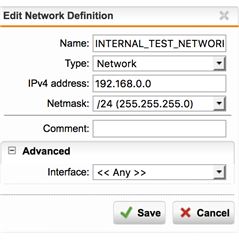
Internal (LAN) 192.168.0.1 /24
Network Services - DNS - Global - Allowed Networks
DMZ Network
LAN Network
Forwarders - DNS Forwarders
Google DNS 1
Google DNS 2
Network Services - DHCP
Interface: Internal
Range Start: 192.168.0.100
Range end: 192.168.0.110
DNS Server 1: 192.168.0.1
Default Gateway: 192.168.0.1
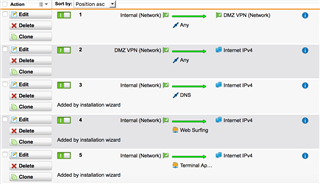
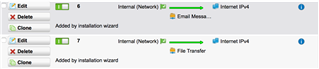
Network Protection - Firewall
Internal Network -> DNS, http, https, http proxy, http Web Cache, ftp, tftp -> Internet IPv4
Internal Network -> Any -> DMZ Network
DMZ Network -> Any -> Internet IPv4
NAT - Masquerading
Internal Network - External WAN
Internal Network - DMZ Network
DMZ Network - External WAN
Web Protection - Web Filtering - Global - Transparent Mode
Allowed Networks
DMZ Network
Internal Network
DMZ Router (VPN Client) Configuration
10.0.0.2
255.0.0.0
GW 10.0.0.1
DNS 10.0.0.1
VPN Client Router in DMZ with IP 10.0.0.2 is connected with External VPN Service. When i connect my Notebook directly to this Router, and set the following ip configuration manually on Notebook
10.0.0.5
255.0.0.0
GW: 10.0.0.2
DNS: 10.0.0.1
I can connect to Internet via VPN Tunnel, works perfect.
But when i connect my Notebook to Internal LAN Network and get via DHCP IP Configuration, 192.168.0.x i can ping to 10.0.0.1 UTM Interface and Router 10.0.0.2.
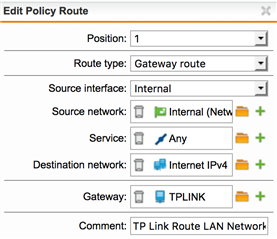
How do i have to adapt the routing and firewall settings in Sophos UTM, that all the access to Internet is routed from 192.168.0.0 /24 over 10.0.0.0 /8 through VPN Tunnel??
Thanks a Lot!
This thread was automatically locked due to age.