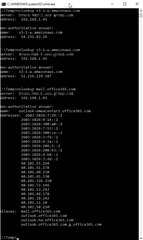
Our system needs to allow outgoing HTTP/S connections to our Amazon S3 services. In the past, I was able to create a "DNS Group" object that kept track of the 700+ IP addresses associated with "s3.amazonaws.com" but now after recent firmware updates the DNS Group object is reduced to just one.
I asked Sophos Support about this behavior, and they responded that the DNS Group object was never designed to track all IPs for a domain name with revolving/rotating or distributed/geo-dependent DNS.
Besides entering all of S3's 300 IP blocks manually as network objects (and updating as they change) I was wondering if anyone uses a solution to remedy this behavior?
How do you block/allow a domain name that has revolving or distributed DNS?
Cheers!
This thread was automatically locked due to age.