Hi all,
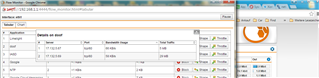
since a few days I have a problem with unwanted traffic originating at the external interface of my UTM. It's destination addresses are from 17.0.0.0/8 (Apple?), the traffic seems to be HTTP (port 80), the application is classified as "doof" (see also screenshots):
1) Does anyone have an idea why the UTM communicates with these addresses?
2) How can I block this traffic (I tried a simple FW rule with the external interface as source, and also an application control rule, but both did not block it).
Any idea?
Thanks a lot,
Klaus.
This thread was automatically locked due to age.