Hello,
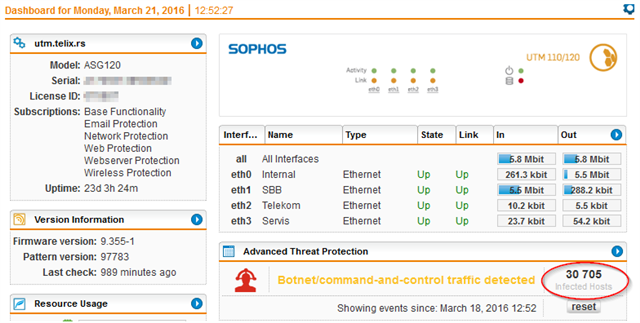
In last couple of days i start receive emails from my Sophos UTM (Firmware version 9.350-12)
A threat has been detected in your network The source IP/host listed below was found to communicate with a potentially malicious site outside your company.
Details about the alert:
Threat name....: C2/Generic-A
Details........: http://www.sophos.com/en-us/threat-center/threat-analyses/viruses-and-spyware/C2~Generic-A.aspx
Time...........: 2016-03-20 06:41:17
Traffic blocked: yes
Source IP address or host: 218.60.112.225
Every Email include different IP Address but it's not my LAN Network. How i can find problematic machine (IP) from my local network ?
This thread was automatically locked due to age.