Hi there
We have a case open with sophos support about this also @ #7525784
After 100's of hours of trying to get SSO working, we believe there is a major problem with the STAS Collector as once users are authenticated - users are then quickly getting removed from the Firewall after a short period of time - say 5 to 10 minutes and therefore are unable to pass traffic through the Firewall.
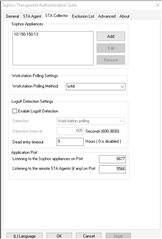
Even with Logoff detection disabled, users are still being dropped, and inside the logs from the STAS Collector, it still shows it trying to find an disable users as below.
I have disabled Log Off detection on the STAS collector, and I have set the dead time at 9 hours - however users get logged off after about 5 minutes. Throughout the logs, the below keeps repeating ; it always checks for expired users and then removes them from the Firewall. Inside the firewall, the users are removed from the tab Definitions & Users > Client Authentication > GLobal , and they are blocked at the firewall from passing traffic.
This issue seems to be well documented throughout these forums .. I would like to know from Sophos what is the solution to this, as I believe the issue is inside the STAS collector - being that by disabled the Log Off detection does not work, and the STAS Collector continues to find and remove users from the Firewall after a period of time. If this issue was fixed, it would work near perfectly.
DEBUG [0x23e4] 9/3/2017 11:22:15 : dca_eventlog: waiting for event log notification
DEBUG [0xea0] 9/3/2017 11:22:16 : dead_entry_timeout_workerthread: Checking for expired users...
DEBUG [0xea0] 9/3/2017 11:22:16 : dead_entry_findExpiredUsers: Username admin.rmorgan+10.200.14.206, CurrentTime 131489113369800000, Stored Time 131489425187143679
DEBUG [0xea0] 9/3/2017 11:22:16 : dead_entry_findExpiredUsers: Username admin.zpole+10.150.100.108, CurrentTime 131489113369800000, Stored Time 131489432936850000
DEBUG [0xea0] 9/3/2017 11:22:16 : dead_entry_findExpiredUsers: Username Administrator+10.150.100.178, CurrentTime 131489113369800000, Stored Time 131489418888420000
DEBUG [0xea0] 9/3/2017 11:22:16 : dead_entry_findExpiredUsers: Username Administrator+10.150.200.57, CurrentTime 131489113369800000, Stored Time 0
DEBUG [0xea0] 9/3/2017 11:22:16 : dead_entry_findExpiredUsers: Username MSwain+10.200.14.207, CurrentTime 131489113369800000, Stored Time 131489316003410000
DEBUG [0xea0] 9/3/2017 11:22:16 : dead_entry_findExpiredUsers: Username SophosSAUZPG-DOC-aaa+10.200.14.111, CurrentTime 131489113369800000, Stored Time 131489427987790000
DEBUG [0xea0] 9/3/2017 11:22:16 : dead_entry_findExpiredUsers: Username zpole+10.200.14.147, CurrentTime 131489113369800000, Stored Time 0
DEBUG [0xea0] 9/3/2017 11:22:16 : dead_entry_findExpiredUsers: 2 expired users found...
DEBUG [0xea0] 9/3/2017 11:22:16 : dead_entry_timeout_workerthread: DeadEntry time expired for the user Administrator Workstation IP 10.150.200.57
ERROR [0xea0] 9/3/2017 11:22:16 : userbd_delete_userinfo: trying to delete user
ERROR [0xea0] 9/3/2017 11:22:16 : userdb_delete_userinfo: UserInfo deleted successfully
INFO [0xea0] 9/3/2017 11:22:16 : remove_user_from_de_repositry: user Administrator with ip 10.150.200.57 removed from DE
DEBUG [0xea0] 9/3/2017 11:22:16 : list_add_tail: first element added
DEBUG [0xea0] 9/3/2017 11:22:16 : dead_entry_timeout_workerthread: DeadEntry time expired for the user zpole Workstation IP 10.200.14.147
ERROR [0xea0] 9/3/2017 11:22:16 : userbd_delete_userinfo: trying to delete user
ERROR [0xb8] 9/3/2017 11:22:16 : USERINFO WAITING INFINITE
DEBUG [0xb8] 9/3/2017 11:22:16 : list_remove_head: last element removed
MSG [0xb8] 9/3/2017 11:22:16 : SSOclient_thread: got userinfo: USER: (null)\Administrator <-> Flags: 4
DEBUG [0xb8] 9/3/2017 11:22:16 : SSOclient_filter_CR_subnet: Entering filter function
DEBUG [0xb8] 9/3/2017 11:22:16 : SSOclient_filter_CR_subnet: authnet not specified, send reqiest to CR
ERROR [0xb8] 9/3/2017 11:22:16 : SSOclient_update_CR: no domain name
ERROR [0xb8] 9/3/2017 11:22:16 : USERNAME Administrator Length 14
ERROR [0xb8] 9/3/2017 11:22:16 : WORKSTN IP 10.150.200.57 Length 14
ERROR [0xb8] 9/3/2017 11:22:16 : SSOclient : PACKET SIZE 213 ㄲ3
DEBUG [0xb8] 9/3/2017 11:22:16 : net_send: bytes sent: 213
DEBUG [0xb8] 9/3/2017 11:22:16 : net_send: full packet sent
MSG [0xb8] 9/3/2017 11:22:16 : SSOclient_thread: Logon/Logout Update sent to: 10.150.150.13:0
ERROR [0xb8] 9/3/2017 11:22:16 : GETTING (USERINFO) FROM QUEUE
DEBUG [0xb8] 9/3/2017 11:22:16 : list_remove_head: list is Empty
ERROR [0xea0] 9/3/2017 11:22:17 : userdb_delete_userinfo: UserInfo deleted successfully
INFO [0xea0] 9/3/2017 11:22:17 : remove_user_from_de_repositry: user zpole with ip 10.200.14.147 removed from DE
DEBUG [0xea0] 9/3/2017 11:22:17 : list_add_tail: first element added
ERROR [0xb8] 9/3/2017 11:22:17 : USERINFO WAITING INFINITE
DEBUG [0xb8] 9/3/2017 11:22:17 : list_remove_head: last element removed
MSG [0xb8] 9/3/2017 11:22:17 : SSOclient_thread: got userinfo: USER: (null)\zpole <-> Flags: 4
DEBUG [0xb8] 9/3/2017 11:22:17 : SSOclient_filter_CR_subnet: Entering filter function
DEBUG [0xb8] 9/3/2017 11:22:17 : SSOclient_filter_CR_subnet: authnet not specified, send reqiest to CR
ERROR [0xb8] 9/3/2017 11:22:17 : SSOclient_update_CR: no domain name
ERROR [0xb8] 9/3/2017 11:22:17 : USERNAME zpole Length 6
ERROR [0xb8] 9/3/2017 11:22:17 : WORKSTN IP 10.200.14.147 Length 14
ERROR [0xb8] 9/3/2017 11:22:17 : SSOclient : PACKET SIZE 165 㘱5
DEBUG [0xb8] 9/3/2017 11:22:17 : net_send: bytes sent: 165
DEBUG [0xb8] 9/3/2017 11:22:17 : net_send: full packet sent
MSG [0xb8] 9/3/2017 11:22:17 : SSOclient_thread: Logon/Logout Update sent to: 10.150.150.13:0
ERROR [0xb8] 9/3/2017 11:22:17 : GETTING (USERINFO) FROM QUEUE
DEBUG [0xb8] 9/3/2017 11:22:17 : list_remove_head: list is Empty
MSG [0x2190] 9/3/2017 11:22:17 : SSO_client_update_heartbeat: cr_node:10.150.150.13 is_active:2
DEBUG [0x2190] 9/3/2017 11:22:17 : net_send: bytes sent: 11
DEBUG [0x2190] 9/3/2017 11:22:17 : net_send: full packet sent
DEBUG [0x23e4] 9/3/2017 11:22:18 : dca_eventlog: received event log notification
DEBUG [0x23e4] 9/3/2017 11:22:18 : dca_eventlog: got security event: ID: 4771 <-> Type: 16
DEBUG [0x23e4] 9/3/2017 11:22:18 : dca_eventlog: waiting for event log notification
DEBUG [0x23e4] 9/3/2017 11:22:22 : dca_eventlog: received event log notification
DEBUG [0x23e4] 9/3/2017 11:22:22 : dca_eventlog: got security event: ID: 4634 <-> Type: 8
DEBUG [0x23e4] 9/3/2017 11:22:22 : dca_eventlog: waiting for event log notification
DEBUG [0x23e4] 9/3/2017 11:22:28 : dca_eventlog: received event log notification
This thread was automatically locked due to age.