Hello,
After configuring the VPN SSL client (as described into the documentation) our SSL VPN clients can't connect to the firewall:
Mon Nov 21 16:35:58 2016 TCP: connect to [AF_INET]x.x.x.x:8443 failed, will try again in 5 seconds: The system tried to join a drive to a directory on a joined drive.
Mon Nov 21 16:36:03 2016 MANAGEMENT: >STATE:1479742563,RESOLVE,,,,,,
Mon Nov 21 16:36:03 2016 MANAGEMENT: >STATE:1479742563,TCP_CONNECT,,,,,,
Mon Nov 21 16:36:13 2016 TCP: connect to [AF_INET]x.x.x.x:8443 failed, will try again in 5 seconds: The system tried to join a drive to a directory on a joined drive.
Mon Nov 21 16:36:18 2016 MANAGEMENT: >STATE:1479742578,RESOLVE,,,,,,
Mon Nov 21 16:36:18 2016 MANAGEMENT: >STATE:1479742578,TCP_CONNECT,,,,,,
Mon Nov 21 16:36:28 2016 TCP: connect to [AF_INET]x.x.x.x:8443 failed, will try again in 5 seconds: The system tried to join a drive to a directory on a joined drive.
Mon Nov 21 16:36:33 2016 MANAGEMENT: >STATE:1479742593,RESOLVE,,,,,,
Mon Nov 21 16:36:33 2016 MANAGEMENT: >STATE:1479742593,TCP_CONNECT,,,,,,
Mon Nov 21 16:36:43 2016 TCP: connect to [AF_INET]x.x.x.x:8443 failed, will try again in 5 seconds: The system tried to join a drive to a directory on a joined drive.
Mon Nov 21 16:36:48 2016 MANAGEMENT: >STATE:1479742608,RESOLVE,,,,,,
Mon Nov 21 16:36:48 2016 MANAGEMENT: >STATE:1479742608,TCP_CONNECT,,,,,,
The firewall is behind a NAT router which forwards the traffic correctly (we tried to setup the tunnel from the LAN too without success).
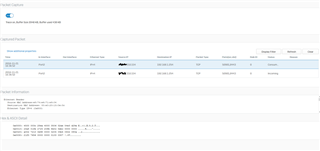
As you can see the PCAP tool logs the 8443 port traffic from the VPN client
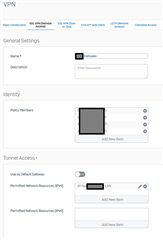
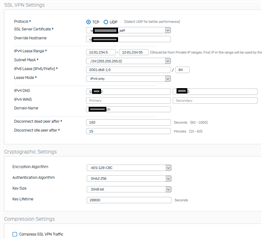
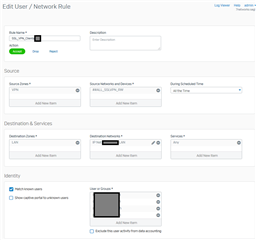
The configuration:
We tried to use a new self signed certificate too, but nothing changes...
Some additional info:
We changed the appliance LAN and WAN IP after the setup wizard.
The appliance is in HA mode.
Thank you for your help.
Stefano
This thread was automatically locked due to age.