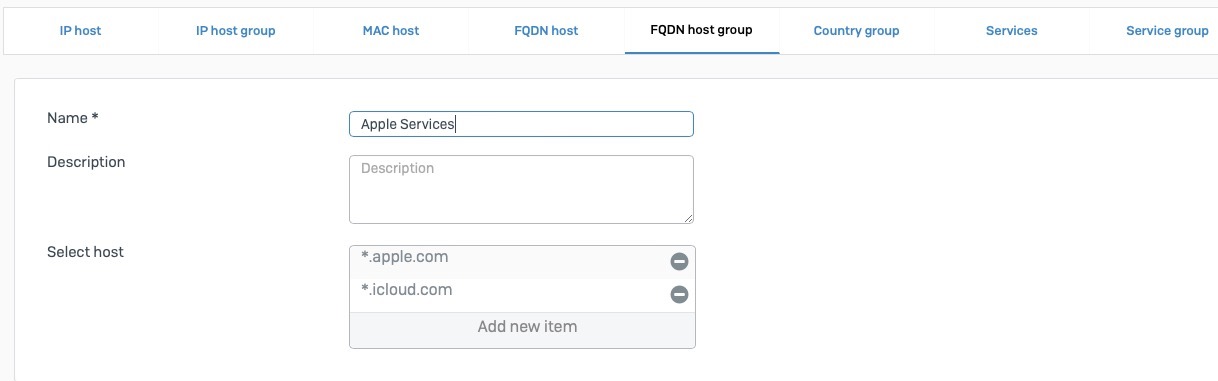
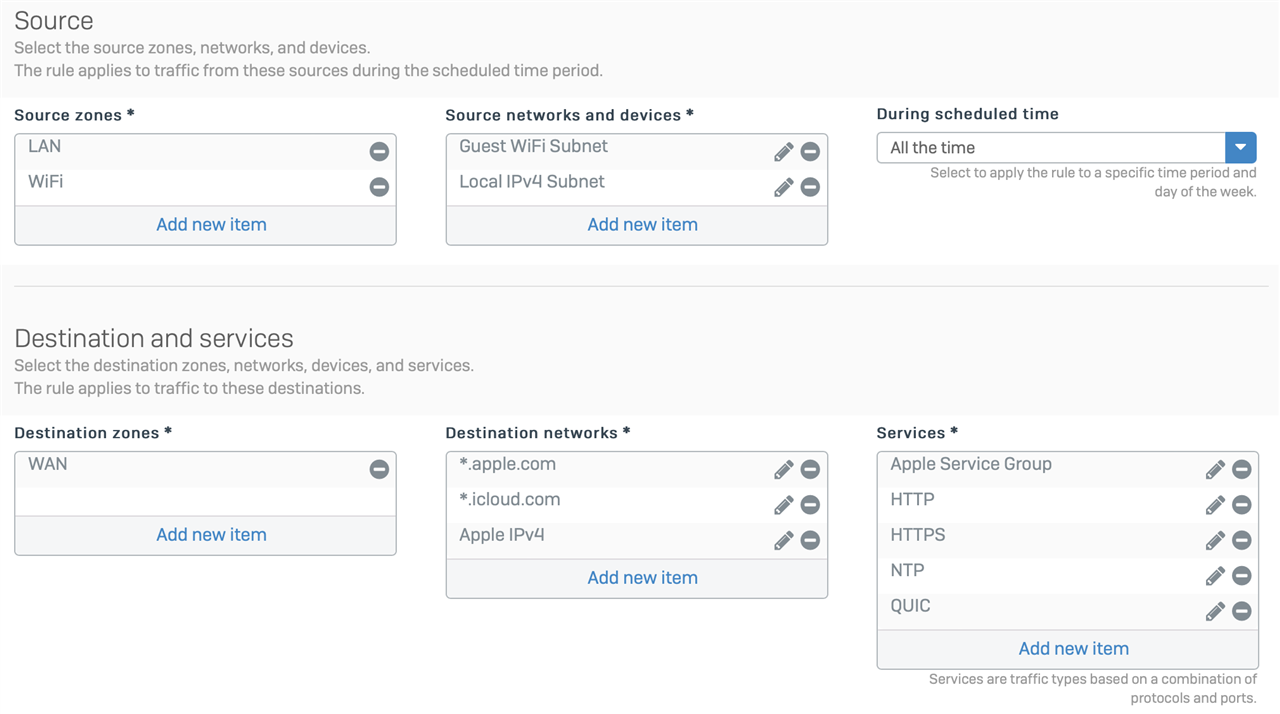
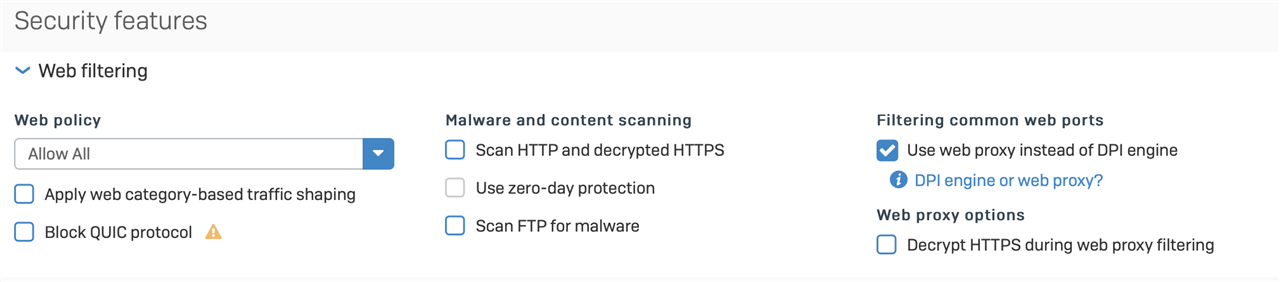
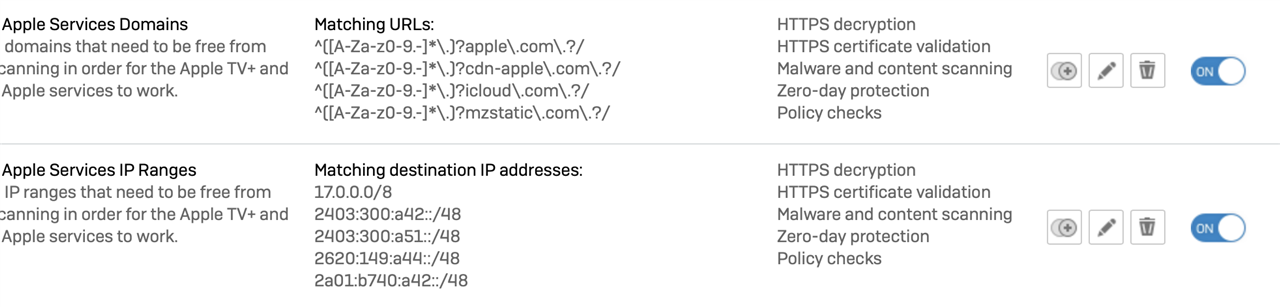
Ok, so I decided to give Apple TV+ a try. I am aware of how finicky Apple products can be, but decided to give it a whirl anyway. Perhaps I'm beating a dead horse on this.
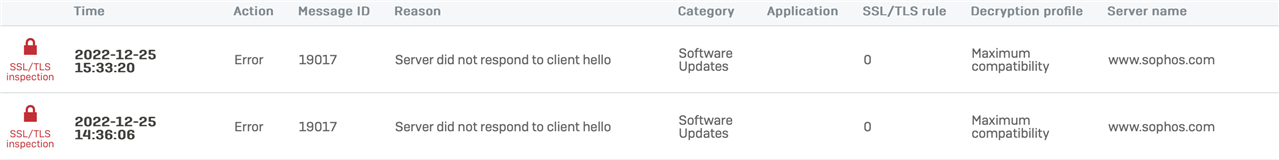
The first issue was the XG blocking QUIC, once I allowed QUIC, streaming seemed to work fine. Then things started going off the rails. I now get intermittent issues where Apple Music and Apple TV+ cannot connect. Apple TV+ provides the following message "Content Unavailable". This occurs no matter if I use an iPad, iMac or Android box.
I use Android boxes with the Apple TV+ app installed.
Apple Music and Apple TV+ drop out every 15 or 20 minutes and they remain gone for several minutes before miraculously connecting. During the Apple down time, the Apple TV+ connection tests pass connecting to the internet but fail with connection to Apple. I can stream using Disney+ with full 4k HDR10 without a single hiccup at any time and no rule exemptions. My Speedtest shows absolutely no issues with my fibre line.
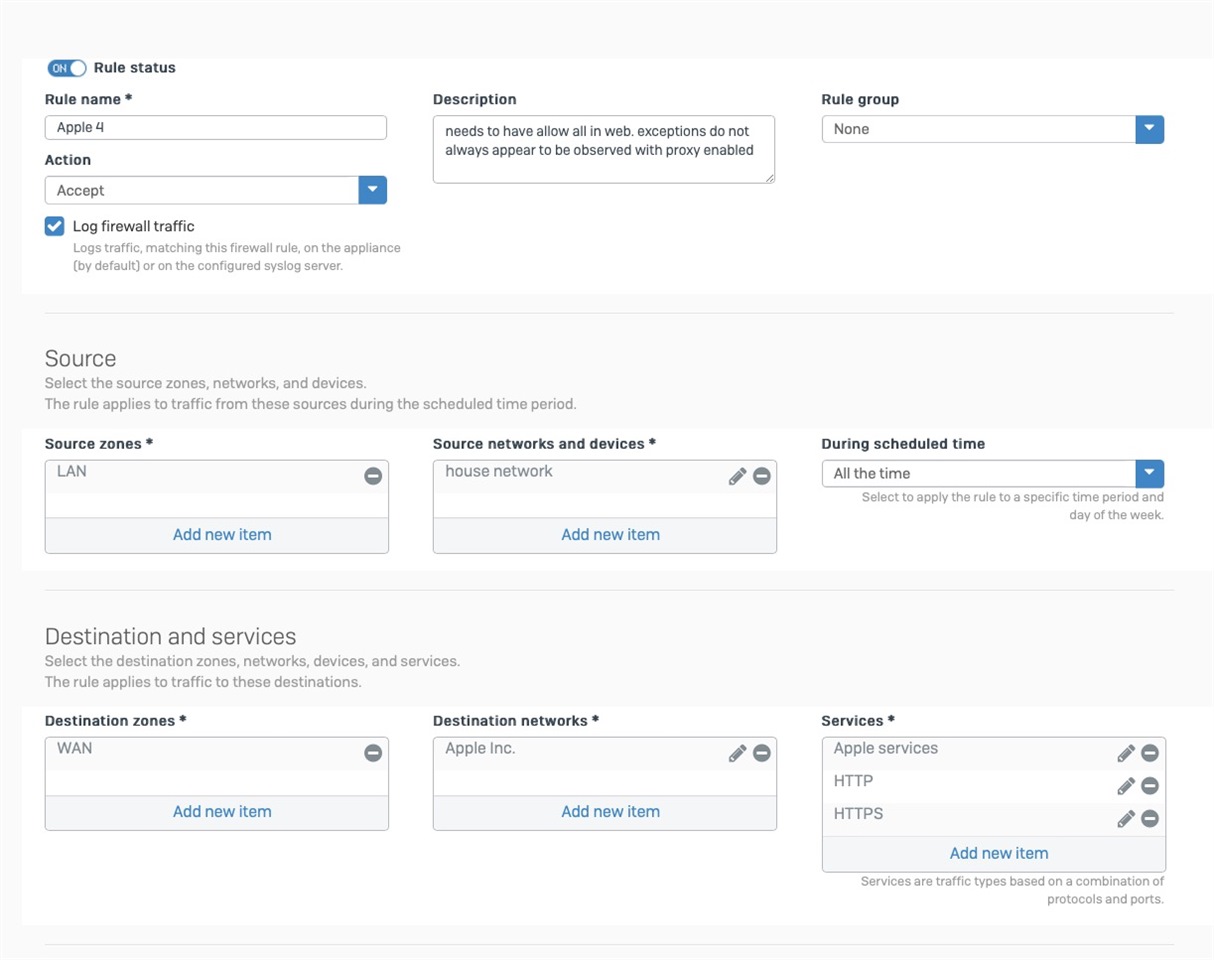
I have tried a number of "troubleshooting" steps with disabling one thing or the other. This became extremely time consuming since the XG takes a very long time to update a firewall rule. To speed things up, I have created the following rule at the top of my rules list:
- LAN to WAN
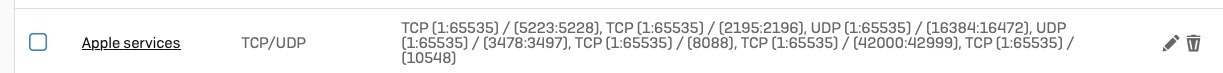
- Allow any service
- Allow any source
- Allow any destination
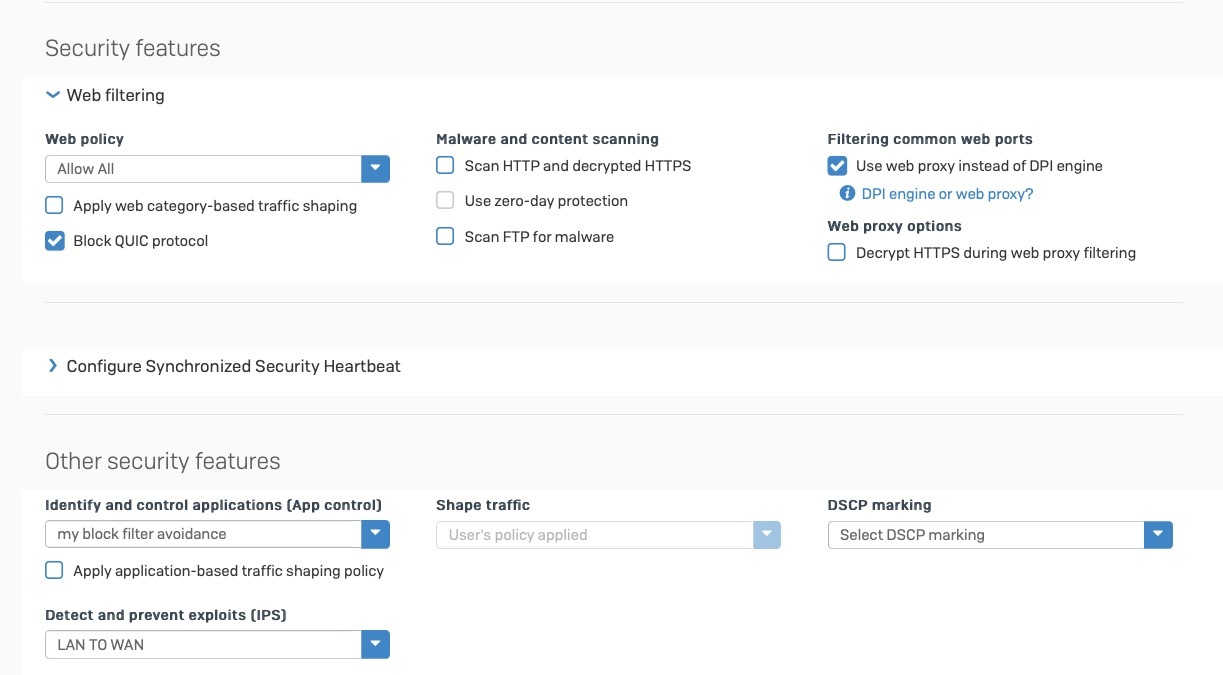
- Web Policy = "Allow All"
- Malware scanning disabled
- Use web proxy instead of DPI
- App Control = "Allow All"
- IPS = "None"
Believe it or not, with the above rule the Apple TV+ and Apple Music still refuse to connect.
At this stage I am at a complete loss as to how to troubleshoot this further. I cannot see how the XG might be interfering with the connection.
I should add that I am attempting to troubleshoot this from my iMac by testing the Apple TV+ app on it.
As I finish typing this post, Apple TV+ & Apple Music both came back online.
This thread was automatically locked due to age.