Perhaps I am missing something simple here, but after setting up WAF for an internal HTTPS server, I am getting the following message when I try to save the rule:
Following domain(s) will not be covered by selected HTTPS certificate
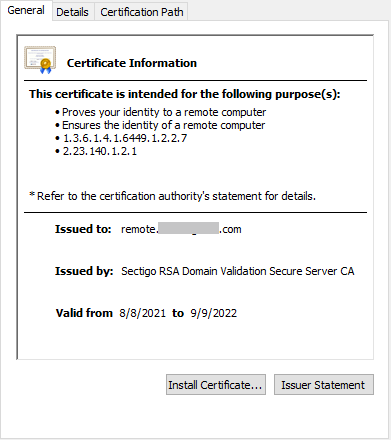
"remote.domainname.com".
1. remote.domainname.com
actual domain removed for privacy of course...
Anyways, I am not sure why the firewall will not use the cert to cover this domain. I generated a CSR with the firewall, got the cert from my provider, uploaded it, and it took it. The provider did provide to me a .crt that I opened and exported as a .cer using windows cert wizard, but that shouldn't matter, right? Also, I know that the WAF needs to have the .key file, but since I generated the CSR with the firewall, it has that already and didn't ask for it when I uploaded the cert.
Also, I checked to make sure that my old DNAT rules do not have 443 included since I understand that I cannot have more than one firewall rule referencing that port. There are other DNAT rules still in place for non-web ports that this application accepts traffic on.
Finally, I have set up the user portal to use a port other than 443, so I don't think there is a conflict there.
The firewall is an XG210 running SFOS 18.0.4 MR-4
This thread was automatically locked due to age.