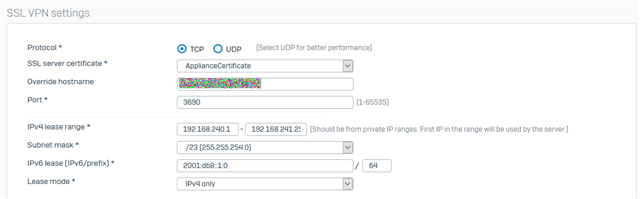
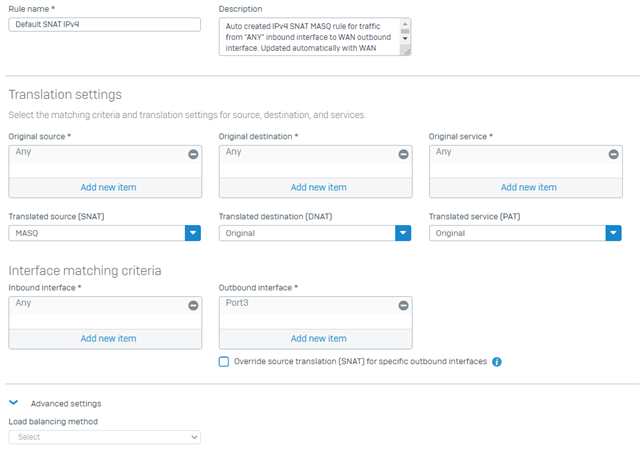
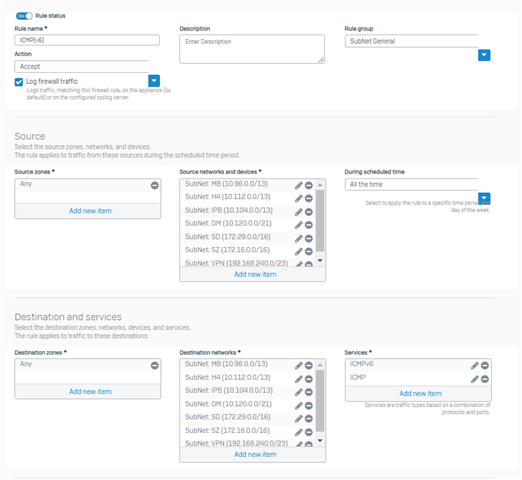
I have enabled SSL VPN ACCESS for IPv4 lease range: 192.168.240.1 - 192.168.241.254.
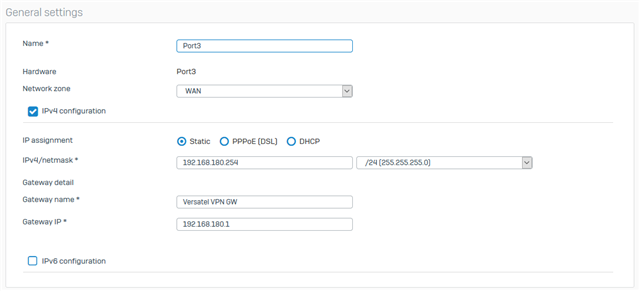
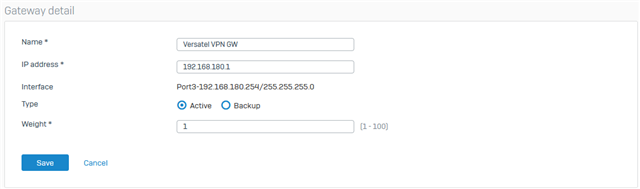
* Port3 is dedicated VPN Port with 192.168.180.254/255.255.255.0 and Gateway 192.168.180.1.
* br0 is 10.99.0.99/13 (Port1 LAN and Port2 WAN) with Gateway 10.99.0.3
If I connect to VPN i'm logging in successfully and i am assigned an IP-Address and connection to LAN works perfectly. Sometimes I get 192.168.240.2; sometimes i get 192.168.240.3 within the Sophos VPN Client. If i get 192.168.240.3 EVERYTHING works as expected - i can ping LAN and other locations (10.112.x.x) connectied via WAN interface; if i get the 192.168.240..2 i can't even ping my WAN network, while LAN is still working. Can you give me an advice how this can be IP related?
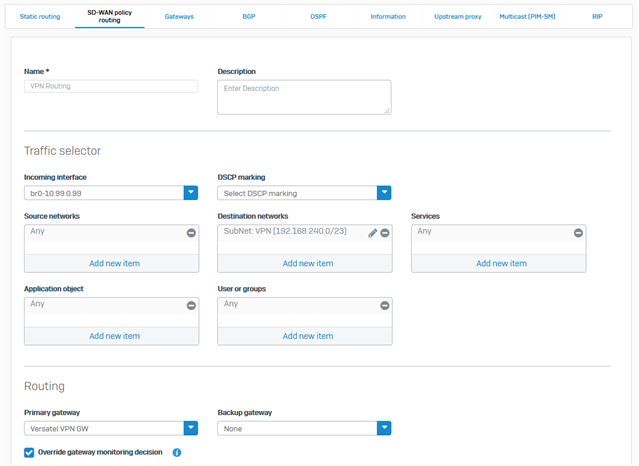
Maybe it's because of the out_interface, which is br0 if i get IP Address 192.168.240.2 and is Port3 for the IP Address 192.168.240.3. Based on the interface the nat_rule_id is 0 if it is NOT working and 3 if it IS working. How is this happening and does anybody know how to solve this?
192.168.240.2 - NOT WORKING
2021-04-30 22:45:18Firewallmessageid="00001" log_type="Firewall" log_component="Firewall Rule" log_subtype="Allowed" status="Allow" con_duration="31" fw_rule_id="43" nat_rule_id="0" policy_type="1" user="a@b.c" user_group="SophosVPNAccess" web_policy_id="0" ips_policy_id="0" appfilter_policy_id="0" app_name="" app_risk="0" app_technology="" app_category="" vlan_id="" ether_type="Unknown (0x0000)" bridge_name="" bridge_display_name="" in_interface="tun0" in_display_interface="tun0" out_interface="br0" out_display_interface="br0" src_mac="40:00:40:01:37:A4" dst_mac="45:00:00:54:47:E6" src_ip="192.168.240.2" src_country="R1" dst_ip="10.112.0.4" dst_country="R1" protocol="ICMP" icmp_type="8" icmp_code="0" packets_sent="2" packets_received="0" bytes_sent="168" bytes_received="0" src_trans_ip="" src_trans_port="0" dst_trans_ip="" dst_trans_port="0" src_zone_type="VPN" src_zone="VPN" dst_zone_type="WAN" dst_zone="WAN" con_direction="" con_event="Stop" con_id="958063232" virt_con_id="" hb_status="No Heartbeat" message="" appresolvedby="Signature" app_is_cloud="0"
192.168.240.3 - WORKING
2021-04-30 22:44:57Firewallmessageid="00001" log_type="Firewall" log_component="Firewall Rule" log_subtype="Allowed" status="Allow" con_duration="62" fw_rule_id="43" nat_rule_id="3" policy_type="1" user="a@b.c" user_group="SophosVPNAccess" web_policy_id="0" ips_policy_id="0" appfilter_policy_id="0" app_name="" app_risk="0" app_technology="" app_category="" vlan_id="" ether_type="Unknown (0x0000)" bridge_name="" bridge_display_name="" in_interface="tun0" in_display_interface="tun0" out_interface="Port3" out_display_interface="VPNPort" src_mac="00:00:80:01:8F:8D" dst_mac="45:00:00:3C:F0:13" src_ip="192.168.240.3" src_country="R1" dst_ip="10.112.0.4" dst_country="R1" protocol="ICMP" icmp_type="8" icmp_code="0" packets_sent="6" packets_received="16" bytes_sent="960" bytes_received="960" src_trans_ip="192.168.180.254" src_trans_port="0" dst_trans_ip="" dst_trans_port="0" src_zone_type="VPN" src_zone="VPN" dst_zone_type="WAN" dst_zone="WAN" con_direction="" con_event="Stop" con_id="3372692800" virt_con_id="" hb_status="No Heartbeat" message="" appresolvedby="Signature" app_is_cloud="0"
This thread was automatically locked due to age.