Hi there. Newbie here. I don't get it.
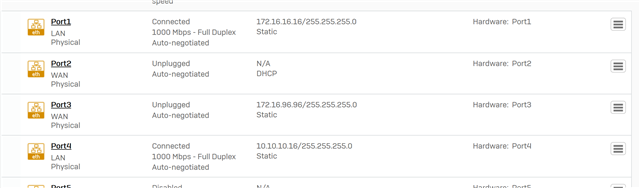
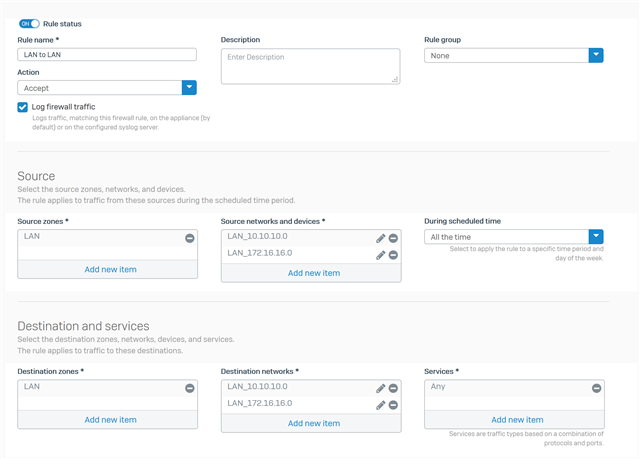
I have two ip ranges in my network 10.0.0.0/24 and 192.168.1.0/24
I've setup the XG210 with the 192.168.1.0 range as LAN and everything works fine except I can't reach the 10.0.0.0 range from 192.168.1.0 range.
How can I remedy this ?
Thanks, Marc
This thread was automatically locked due to age.