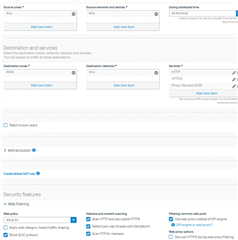
I upgraded an XG to v18 yesterday.
Since the update, access to the Internet, for the CLients on the LAN, no longer works.
The clients use an explicit proxy server (XG).
At first I thought there was a problem with the migrated NAT rules, I deleted all superfluous ones and currently used the default snat rule. But to get the clients to the internet I had to add HTTP and HTTPS to the destination in addition to TCP_3128.
Otherwise I got the message that the proxy server did not react.
Does anyone have any idea what could be the reason for this?
Translated with www.DeepL.com/Translator (free version)
This thread was automatically locked due to age.