This is a continuation of https://community.sophos.com/products/xg-firewall/f/firewall-and-policies/109122/failing-pci-scans-because-of-outdated-jquery-in-user-portal---is-there-a-fix/391323#391323 but a new thread was requested by LuCar Toni here: https://community.sophos.com/products/xg-firewall/f/firewall-and-policies/109122/failing-pci-scans-because-of-outdated-jquery-in-user-portal---is-there-a-fix/392533#392533
On a fresh install of any firmware to a XG appliance the WAF settings allow insecure protocols and 3DES in addition to Trace/Track. This has been a issue going back over two years (previous post: : https://community.sophos.com/products/xg-firewall/f/firewall-and-policies/84480/failing-pci-scans---how-do-i-disable-tls-1-0-and-block-des-3des/368398#368398 )
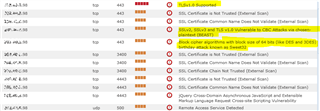
Demonstration of what is happening. After any firmware upgrade I have a PCI compliance scan done and get the following results:
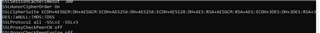
I highlighted the failures on 3DES and TLS 1.0. So I telnet in and check the appache httpd.conf file and this is whats in it:
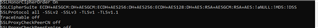
Sure enough all those protocols are reenabled on each firmware upgrade. I then manually edit that file to remove 3DES, TLSv1, TLSv1.1, and TraceTrack so it looks like this:
and restart the services (per instructions support gave me and I blogged about here). I then rescan and I no longer fail due to those items:
This is happening to multiple people on this forum and who have commented on my blog post. Settings within the UI (mainly the "TLS setting") do not affect this behavior.
This is happening on 3 seperate XG boxes, one XG310 and a pair of XG125w. All three were installed at different times and the last XG125W shipped with v17, the other two started with v16. All three exhibit the same behavior on each firmware upgrade, the "secure" settings get wiped out and replaced by a "insecure set".
[locked by: FloSupport at 7:33 PM (GMT -8) on 11 Jan 2019]