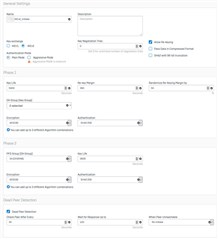
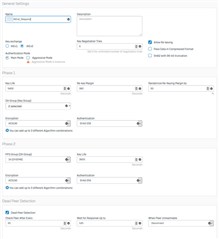
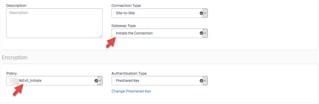
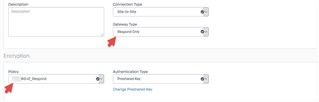
For those who asked, our VPN setup is the result of the intervention of 2 seniors engineers at Sophos, Boston. I normally need no help to setup a IKEv2 VPN. I was doing it with no sweat on any firewall more than a decade ago.
This thread was automatically locked due to age.