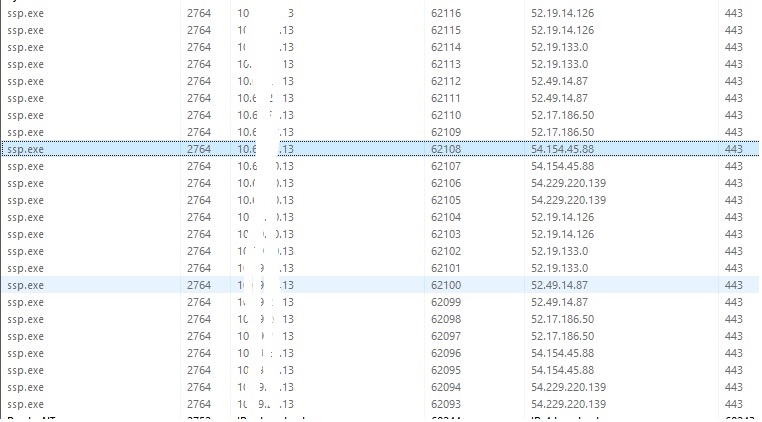
We have been investigating issues with our firewalls and one thing I noticed is i have been seeing hundred and hundred of hits from ssp.exe to our firewall
Client base is over 500!
These seem to be amazon IP Address, why is it talkign too these and what is ssp.exe?
This thread was automatically locked due to age.