Hi
In an attempt to deploy some Data Loss Protection Rules we are having an issue
Situation
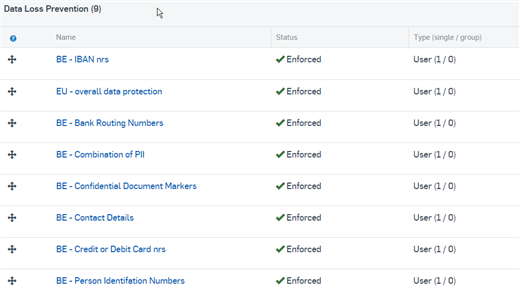
We created 6 Content Rules for Belgium region to block content
Accordingly 6 Word documents were created with content to test the rules
Policies were enforced and assigned to a test user
1. IBAN nrs
2. Bank Routing Nrs
3. Combination of PII
4. Contact details
5. Credit or Debit card nrs
6. PINs
Additionally 1 File rule for Europe region was created to block all file transfers
Issue
We would expect the rules to be executed from top to bottom as indicated in Sophos Central.
However during our tests it seems only the first rule (on top) is checked. All the rest is not processed anymore:
E.g.: The content rule for IBAN nrs is on top >> Only the word file containing IBAN nrs is blocked. All rest is allowed without any message from Sophos.
However when we put the the content rule for Bank Routing nrs on top >> Only the word file containing BIC nrs is blocked and again all rest is allowed.
Please see the screenshot giving some elucidation on the setup:
Question
How can we have each separate document tested against each of the rules and not only the top one rule.
It looks like DLP stops processing rules after the top one.
This thread was automatically locked due to age.